In the ever-evolving landscape of digital marketing, one of the biggest challenges faced by businesses is the menace of click fraud. Click fraud refers to the malicious and fraudulent clicking on online advertisements, with the sole purpose of depleting an advertiser’s budget or sabotaging their marketing efforts. As businesses invest substantial resources in online advertising campaigns to amplify their marketing impact, it becomes imperative to shield these ads from click fraud and ensure that marketing budgets are utilized effectively. Click fraud can have severe consequences for businesses. Not only does it drain advertising budgets, but it also skews valuable data and analytics, making it difficult to assess the true effectiveness of a campaign. Moreover, it can lead to a decrease in the return on investment (ROI) for marketing initiatives, hindering business growth. To combat this menace and protect their marketing efforts, businesses need to implement robust strategies and tools.
One effective approach to shield ads from click fraud is through the use of click fraud detection and prevention software. These sophisticated tools employ advanced algorithms and machine learning techniques to analyze click patterns, identify suspicious activity and distinguish between genuine clicks and fraudulent ones. By monitoring various parameters such as IP addresses, device types and browsing behavior, these tools can quickly flag and filter out fraudulent clicks, ensuring that businesses are not charged for invalid traffic. Additionally, businesses can employ proactive measures to minimize the risk of click fraud. One such measure is the implementation of stringent ad placement strategies. By carefully selecting reputable websites and platforms to display their ads, businesses can minimize the chances of their ads being exposed to fraudulent activities. Partnering with trusted advertising networks and publishers can also contribute to creating a safer environment for online ads. Furthermore, ongoing monitoring and analysis of advertising campaigns are crucial in detecting and addressing click fraud. By regularly reviewing campaign metrics and performance indicators, businesses can identify irregularities or sudden spikes in click activity that may indicate fraudulent behavior. This allows them to take prompt action and mitigate potential losses.
Education and awareness among advertisers and marketing teams are equally important in the fight against click fraud. By staying updated on the latest trends and techniques employed by fraudsters, businesses can develop proactive strategies to stay one step ahead. Training employees to recognize and report suspicious activity can contribute to a collective effort in combating click fraud protection. In conclusion, click fraud poses a significant threat to businesses’ online advertising efforts. However, with the right tools, strategies and vigilance, it is possible to shield ads from click fraud and maximize the impact of marketing campaigns. By leveraging click fraud detection and prevention software, implementing proactive measures, monitoring campaigns and fostering awareness, businesses can protect their advertising investments and drive meaningful results in the digital realm.
In the vast digital landscape of our modern world, where data is the lifeblood of organizations and individuals alike, the art of data recovery stands as a beacon of hope amidst the shadows of lost information. The chronicles of data recovery are filled with epic tales of resilience, ingenuity and unwavering determination to restore what was once thought irretrievable. In the annals of data recovery, there lies the tale of a renowned tech wizard named Alexia. Her reputation preceded her as she embarked on a seemingly impossible mission to recover vital data from a company’s crashed server. The stakes were high as the company’s entire financial records were at stake and failure would mean their demise. Undeterred by the daunting challenge, Alexia delved into the depths of the server’s damaged hardware and meticulously reconstructed its intricate components. With her vast knowledge of data structures and file systems, she embarked on a painstaking journey of data reconstruction.

Hours turned into days and days into weeks as she tirelessly worked to extract fragments of information from the tangled wreckage and you could check here https://pierrepirol.com/. Her efforts bore fruit as she managed to recover the majority of the lost data, restoring the company’s financial stability and earning her a place among the legends of data recovery. Another tale unfolds in the realm of personal devices, where a hapless photographer named Ryan found himself on the brink of despair when his external hard drive, containing years’ worth of priceless memories, suddenly failed. Determined to salvage his cherished photographs, Ryan sought the expertise of a renowned data recovery specialist named Dr. Amelia. Armed with an arsenal of cutting-edge tools and forensic techniques, Dr. Amelia embarked on a digital quest to retrieve the lost images. She meticulously examined the damaged drive, scanning each magnetic platter for the faintest traces of data. Her journey took her through complex algorithms and intricate data recovery methods as she pieced together the fragments of Ryan’s photographic history.
With unwavering dedication, Dr. Amelia managed to recover the vast majority of the lost images, bringing joy and relief to Ryan’s heart and immortalizing her name in the realm of data recovery heroes. These epic tales of data recovery chronicle the triumph of human resilience and expertise in the face of technological adversity. They serve as a testament to the indomitable spirit that drives us to reclaim what is lost, to unravel the mysteries of damaged devices and to resurrect the fragments of digital existence. In a world where the value of information knows no bounds, these chronicles stand as reminders that, with skill, perseverance and a touch of magic, even the most dire data disasters can be transformed into tales of redemption.
When encountering an api-ms-win-crt-runtime-l1-1-0.dll Access Violation error, it indicates that an application or process is attempting to access the api-ms-win-crt-runtime-l1-1-0.dll file in an unauthorized or incorrect manner. An access violation occurs when a program attempts to read from or write to a memory address that it does not have permission to access. Here’s a closer look at this error and potential solutions:
Causes of the error:
- Corrupted or missing DLL file: If the api-ms-win-crt-runtime-l1-1-0.dll file is corrupted, missing, or incompatible, it can result in an access violation error.
- Memory issues: Insufficient memory, faulty RAM, or other memory-related problems can cause access violations when attempting to access the DLL file.
- Software conflicts: Conflicts between different versions of the Visual C++ Redistributable package or other software components can lead to access violation errors.
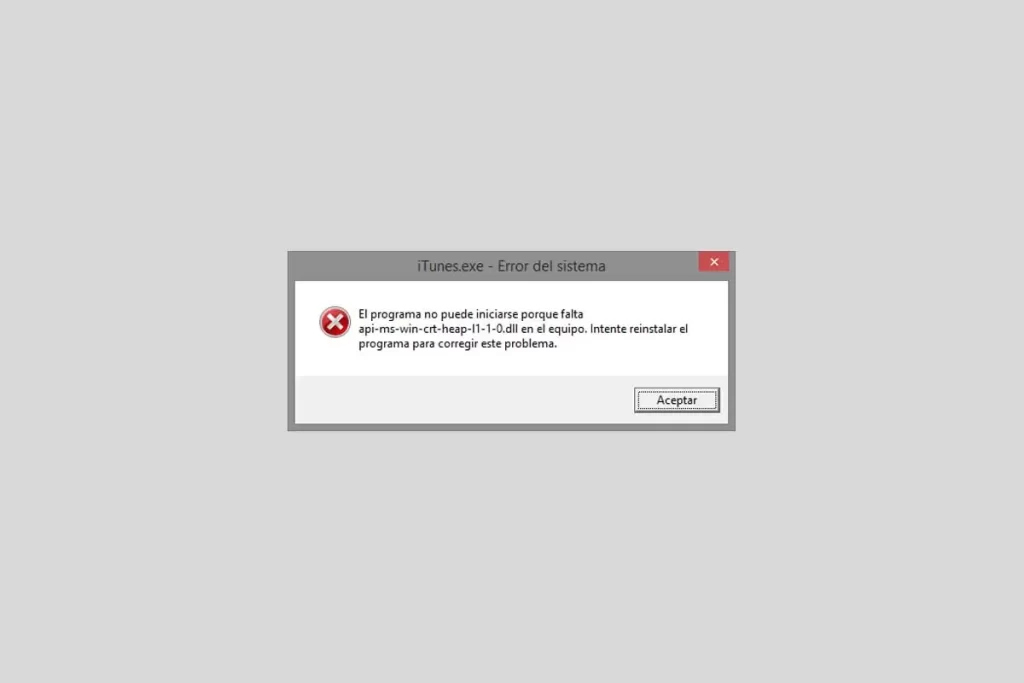
Error messages and symptoms: When encountering an api-ms-win-crt-runtime-l1-1-0.dll Access Violation error, you may see error messages such as:
- The instruction at [memory address] referenced memory at [memory address]. The memory could not be read/written.
- Application crashes or freezes.
Solutions to resolve the error:
- Update the Visual C++ Redistributable: Ensure that you have the latest version of the Visual C++ Redistributable package installed. Download and install the appropriate version from the official Microsoft website or the software vendor’s website.
- Repair or reinstall the Visual C++ Redistributable: If you already have the Visual C++ Redistributable package installed, try repairing or reinstalling it. Go to Control Panel > Programs > Programs and Features, locate the Visual C++ Redistributable package in the list, right-click, and select Repair or Uninstall followed by a fresh installation.
- Perform a clean boot: A clean boot starts the computer with a minimal set of drivers and startup programs, which can help identify and resolve software conflicts. Follow the steps outlined in Microsoft’s official documentation to perform a clean boot.
- Check for memory issues: Run a memory diagnostic tool, such as Windows Memory Diagnostic, to check for any memory-related problems. If faulty RAM is detected, consider replacing it.
- Update drivers and Windows: Ensure that your system has the latest updates installed, including drivers and Windows updates. Outdated or incompatible drivers can cause access violations.
- Scan for malware: Perform a thorough scan of your system using reliable antivirus or antimalware software. Malware infections can interfere with api-ms-win-crt-runtime-l1-1-0.dll files and cause access violations.
- Seek expert assistance: If the error persists despite trying the above solutions, it is recommended to seek assistance from technical support or the software vendor. They can provide specialized guidance and help diagnose and resolve the issue based on your specific system configuration and application requirements.
It is important to note that an access violation error can be caused by various factors, and the solutions provided may not always resolve the issue. In such cases, seeking expert assistance is crucial to effectively diagnose and fix the problem.
With the achievements of the touch screen phones and pills, digital graphical and painting actions become a little more well-liked. Aside from observing video lessons or editing and enhancing images, painting can be considered as being the most artistic exercise on portable digital gadgets. Digital painting produces in us numbers of powerful tools and has. Many digital painting methods do not exist in standard painting art. We are able to see a lot of digital performers making amazing artworks, with awesome effects and colors. Beginning on computers masterpieces, together with the flourishing of cellular digital products mobile phones and tablet pcs digital painting gets now ever more popular amongst musicians, makers and art lovers. Painting applications operating on mobile phones be more adaptable, and also stronger.
Apart from fundamental painting software for the kids or definite first-timers, good quality skilled software are available out there. The expert application levels need to supply a lot more choices and has on the users. However with more possibilities featuring, the applications become a little more advanced plus more complicate to use. On this page I will discuss this issue which I do take into account being the center of painting applications: the remember dream ai art generator to brush results. I will not enumerate the thousands different types of brush heads. Actually I will attempt to explain how they work and the way they can be arranged. About the lower clean cerebrovascular accident created using communities, we could then add different versions of their aspect:
The size: numerous applications provide the likelihood to alter the actual size of the remember to brush by using a cursor or another appropriate tool. You will also find some software, to get a reason of simplexes, predetermined every one of the remember to brush sizes, then the end user cannot adapt them, but will decide on between numerous preselected brushes in accordance with their sizing. Each of the 2 remedies have its advantages, it is a question of developer’s selection.
The opacity color saturation: this parameter will prove to add or eliminate transparency on the hues. To reduce out one, you only increase transparency. Along with Per cent of transparency, the colour is completely opaque 100% saturation.
The area in between 2 clean heads: this parameter will bring you wrongly identified as the opacity adjustment. The truth is, visually opacity and spacing make the very same outcome, but are totally different. Why space create opacity? When you overlay a number of very low-density images, you will certainly get a darker image. Inside the contrary, when you boost the opacity saturation of a very low-occurrence impression, it darkens way too.
The Dark Web is a hidden and anonymous part of the internet that is not accessible by traditional search engines or browsers. It is a network of websites and online communities that require special software and authentication to access. While the Dark Web is often associated with illegal activities, such as drug trafficking and illegal firearms trading, it is also used for legitimate purposes, such as online privacy and political activism. In this article, we will explore what you need to know about the Dark Web. Firstly, it is important to understand that the Dark Web is not the same as the Deep Web. The Deep Web refers to any website or online content that is not indexed by search engines, including private databases, email accounts, and banking records. The Dark Web, on the other hand, refers specifically to websites that are intentionally hidden and require special software to access. To access the Dark Web, users need to use a special browser called Tor The Onion Router. Tor uses a complex system of encryption and routing to conceal the user’s IP address and location, making it nearly impossible for anyone to trace their online activity.

While Tor was initially developed by the US government for secure communication, it is now used by activists, journalists, and others who require online anonymity. One of the biggest misconceptions about the Dark Web is that it is exclusively used for illegal activities. While it is true that there are illegal marketplaces, forums, and chat rooms on the Dark Web, there are also legitimate uses for the anonymity it hidden wiki provides. While it is possible to access the Dark Web, it is not without risk. For one, the anonymity provided by Tor can be a double-edged sword. While it can protect users from government surveillance and censorship, it can also make it easier for criminals to carry out illegal activities. Additionally, many Dark Web sites contain malware, scams, and other threats that can compromise the user’s computer and personal information.
It is also important to note that accessing the Dark Web may be illegal in some countries. In the US, for example, there are no laws against accessing the Dark Web, but certain activities, such as buying illegal drugs, are illegal regardless of the medium used. In other countries, such as China and Iran, the use of Tor is heavily restricted, and accessing the Dark Web can result in severe penalties. In conclusion, the Dark Web is a hidden and anonymous part of the internet that is not accessible by traditional search engines or browsers. While it is often associated with illegal activities, there are also legitimate uses for the anonymity it provides. However, accessing the Dark Web is not without risk, and users should be aware of the potential dangers and legal implications before venturing into this hidden world.
Computers and PC programming can promptly become obsolete, requiring invigorates to ensure that everything is running right. The explanation for the Windows Update feature is to allow Windows clients on laptops get the updates that they need for security, programming and other near purposes. Microsoft Windows consistently conveys their reports on Tuesdays, and these updates are usually a mixed bag of security redesigns, support improvements and various updates made to the product and working system running on your PC. It is indispensable to guarantee that you are using the most critical of these updates to keep your PC running right. Windows update dispatches simply work for computers running Microsoft Windows working structures, for instance, Microsoft Windows 95, Microsoft Windows 98, Microsoft Windows 2000, Microsoft Windows XP, Microsoft Windows and Microsoft Windows 11.
Keeping the functioning structure invigorated is basic, whether or not you feel like it may not be fundamental. Overall when your PC downloads the updates, Windows will give you a talk that grants you to see which updates are for the most part huge and which are not. This can help you with finishing up which updates to acquaint and which not with worry about, which a huge is thought depending upon the sorts of updates that are open to you. Your task bar will have a popup that tells you that Windows invigorates are ready for foundation.
You can tap on the little image here and it will raise a trade box. The talk box will tell you the quantity of windows update decisions are essential and the quantity of are simply optional. You can go down the whole summary of updates and check or uncheck the cases anyway you see fit, that you are simply presenting the updates that you are enthusiastic about. Click presents, and Windows will begin the most widely recognized approach to invigorating and read here http://www.trishwise.com/2023/how-to-get-win-11-for-compatible-pc-things-to-know.htm. At the point when the Windows update installer is done, it will induce you for a restart. You all around need to reboot your PC after you do an update for all of the new security invigorates and other programming updates to create results. You can see Windows that you would prefer not to reboot your PC right away, yet you should reboot it at the earliest open door so you can start capitalizing on the new security invigorates that you presented and all of the benefits that they offer of real value for you.
Current news says that a General Blaze Recovery device is on the way maintain a wide variety of blast based limit contraption like flash memory, SSD, SD card, CF card, This is a progression data recovery plan in the world for streak memory based limit devices. Close by the fast improvement of development, streak based limit contraptions become more connected with our step by step like, from SD card, CF card to USB streak circle, streak memory. To store those essential data related in work or life, by far most have a couple of USB circles with different limit limits. Identical to other limit devices, there is also the risk of data loss of flicker memory. As you would be aware, a direct data disaster case can be recovered through a few savvy data recovery programming, regardless, goes to the case that the gleam memory cannot be seen by PC where these genuine data recovery programming would not ever work.
There are by and by many flash memory recovery mechanical assemblies out there, yet that’s what a tremendous deformity is, the preposterous limitation of assist with posting even planned one of each and every ten with the burst memory course of action open in market. By virtue of the requirement of assist list, various clients with having negative perspectives on these instruments, saying that they are not smart. The crucial issue that makes data recovery irksome is that the chip embedded in streak memory. The method embraced in current devices is to look at streak memory chips byte by byte to know better of the data accumulating number shuffling from the chips, the really convincing response for data recovery can be worked out. There is a differentiation between streak memory and hard drive where hard drive can be made by two or three serious makers, of course, the extras are at this point using the strategy expected for Cyber Security hard drive fix instruments.
That is the explanation such gadgets would not have the choice to find a good pace as a general rule, paying little mind to how troublesome work was made to improve or give revives by those producers. As we probably know, the cost of glint memory is reasonably low and less development serious. As of now a few thousand dealers are giving flash memory game plan which implies a huge number models and brands should be visible any place watching out, even a lone vendor has particular blast memory game plan which infers the data storing calculating is reasonable phenomenal. For this present circumstance to figure out a response from different number shuffling is by no means whatsoever, so smart. As needs be paying little heed to how they revive or work on their things and soon it will turn out unsatisfied by their clients. Clearly, a couple of creators keep conveying these things on helping reason by their update variations.
Are you thinking about a career in me . T, however you are also enthusiastic about security? In case you are there is a way to merge both and acquire a job that you simply will love and revel in. To merge both you might in fact operate in the field of info stability. As the number of hackers continues to rise every year, businesses are continually needing folks to make certain that their system and information about their company and consumers are secure and this is why you may be found in. Even so, developing a wish to merge both is not ample as there is also the requirement for getting the capabilities and methods needed to counteract and protect against the activities of online hackers. Among the finest techniques to accomplish this is to turn out to be accredited, and if this is the route you are interested in there are certainly many qualification choices accessible to you, below are a few:
CEH – This qualification is called the Accredited Ethical Hacker and is perfect for stability officials, website managers, and auditors and merely about anyone who involves the sincerity of the network of the company’s system. To become licensed in this region persons can experience five days of rigorous CEH instruction exactly where they will be explained how to examination, scan and hack a company’s group and but measures set up so it will be much less vulnerable. The target of the degree of education will be the tools and systems involved in hacking.
ECSA – This is basically the EC-Authorities Licensed Safety Analyst certification which is more advanced compared to the CEH. Whilst the CEH qualification focuses on educating people concerning the systems and instruments linked to hacking, ECSA usually takes it up yet another notch by equipping individuals together with the strategy expected to critically determine the result of the instruments and technologies. By using this expertise, hire a hacker to fix credit score students will therefore have the ability to execute extensive assessments which can be required for check and protect the company’s network from hackers. It is for that reason ideal for info testers, risk examination specialists, group web server administrators, program administrators and firewall administrators.
LPT – The Certified Penetration Tester is definitely the highest measure of certification for contra –hackers. To experience this amount of recognition you would need to get the two certification mentioned before. This program generally intends to supply individuals using the best techniques and procedures utilized in the protection sector. Using this amount of certification individuals provide talking to and penetration tests worldwide and also conducts and rehearse security screening in companies recommended by EC-Council. As a way to acquire hacker training for these recognition you would probably could opt to experience a 5 time extensive education exactly where you will not simply be taught the idea engaged at every level but would also obtain on the job coaching.
The PC forensics market should experience an upsurge by prudence of the extension in complex digital wrongdoing and manipulator attacks and monetary improvement in non-modern countries. PC forensics which insinuates examination and itemizing of digital data for a genuine item is the most perceptible market inside the as a rule criminological market. PC forensics has turned into a ton of dynamic in the field of digital wrongdoing, to play out a coordinated assessment, to recognize hidden away real factors for definite assessment results. A grouping of strategies is used by inspectors to evaluate and glance through hidden away, mixed or eradicated records or coordinators. Consequently, producers are exploring imaginative things and organizations to invigorate their market presence and satisfy the creating need.
PC forensics have furthermore gained universality in non-modern countries, for instance, India and China owing to the extended burglary risks and digital wrongdoings, joined with extended states utilization in digitalization of regions like banking, guideline execution, watchman, and information development, among others. Climb in optional income and extension in the amount of shown clients has similarly upgraded the Forensics advancement of the market in the locale. The proposition of PC forensics as a requirement for fitting assessment by government affiliations has in no time extended their gathering rate in both made and making economies.

For instance, to stay aware of reliability, the conditions of different countries in areas, for instance, China and Brazil among others have outlined new rules that rely upon the permission to data and discipline because of adjustment of data or wrong segment in data records. To battle with spread out players, various makers like Illustration Organization, Twofold Understanding, and Digital Examiners, among others mean to cultivate new PC quantifiable contraptions to secure purchaser interest and augmentation their piece of the general business forensic audio analysis. In any case, the vital part on the lookout, for instance, Access Data Get-together Inc., Course Programming, Inc., and Log Beat Inc. have been utilizing economies of scale to fulfill the rising requirement for PC quantifiable. The spread out brands have taken on thing ship off, associations, and business expansion as their improvement procedure to build up their footing keeping watch. The essential place of this thing ship off was to reveal the redesigned component of this item among buyers, to obtain popularity keeping watch. Anyway, rising unpredictability of mobile phones and extended utilization of cloud based applications could hamper the improvement of digital forensics market.
A supervisor will have numerous things on their plate and will need to designate liabilities to team individuals so as not to overpower anybody. A team director will observe the abilities and gifts of their individuals. They will actually want to perceive who can finish what the correct way the initial time. It is vital to perceive every individual for what they can bring to the project. Individuals who do not take an interest or are a channel in the team ought to be supplanted with other people who can be propelled and who are committed to arriving at the objective introduced before them. The primary thing that should be done is the team should conclude what the issues really are. A project would not be without its concerns. An issue is normally which begins the execution of an arrangement. The issues are characterized and arrangements are looked for. With the commitment of each and every part, the arrangements are coordinated such that they will fix the issues without adding more.

It is generally smart to ensure that you take care of each and every base and considered numerous things that could come as deterrents during the execution of the arrangement quite a bit early. Along these lines, in the event that something occurs, there is an arrangement that will cover it. A decent project supervisor will watch the arrangement as it is set in motion. They will screen the advancement of their team individuals and search for any potential issues that were not considered already. Assuming there are unanticipated issues, individuals can give info and assist with settling the issues.
They might be the ones who will get the issue before it becomes wild. A pioneer will need to put the top and proficient individuals in their team to take care of business and how to build trust in a remote team. They would not have any desire to take on every one of the actual subtleties, particularly since they will be assuming a sense of ownership with the consequences of the project. From the decision making to the association to execution and determination of the project, a team chief will need to track down the absolute most ideal individuals from their team to add to the team and will need to pay attention to the thoughts in general and hypotheses they might have. It means a lot to pursue a similar objective. Participation ought to continuously be supported by the pioneer and strived for as a team part.






